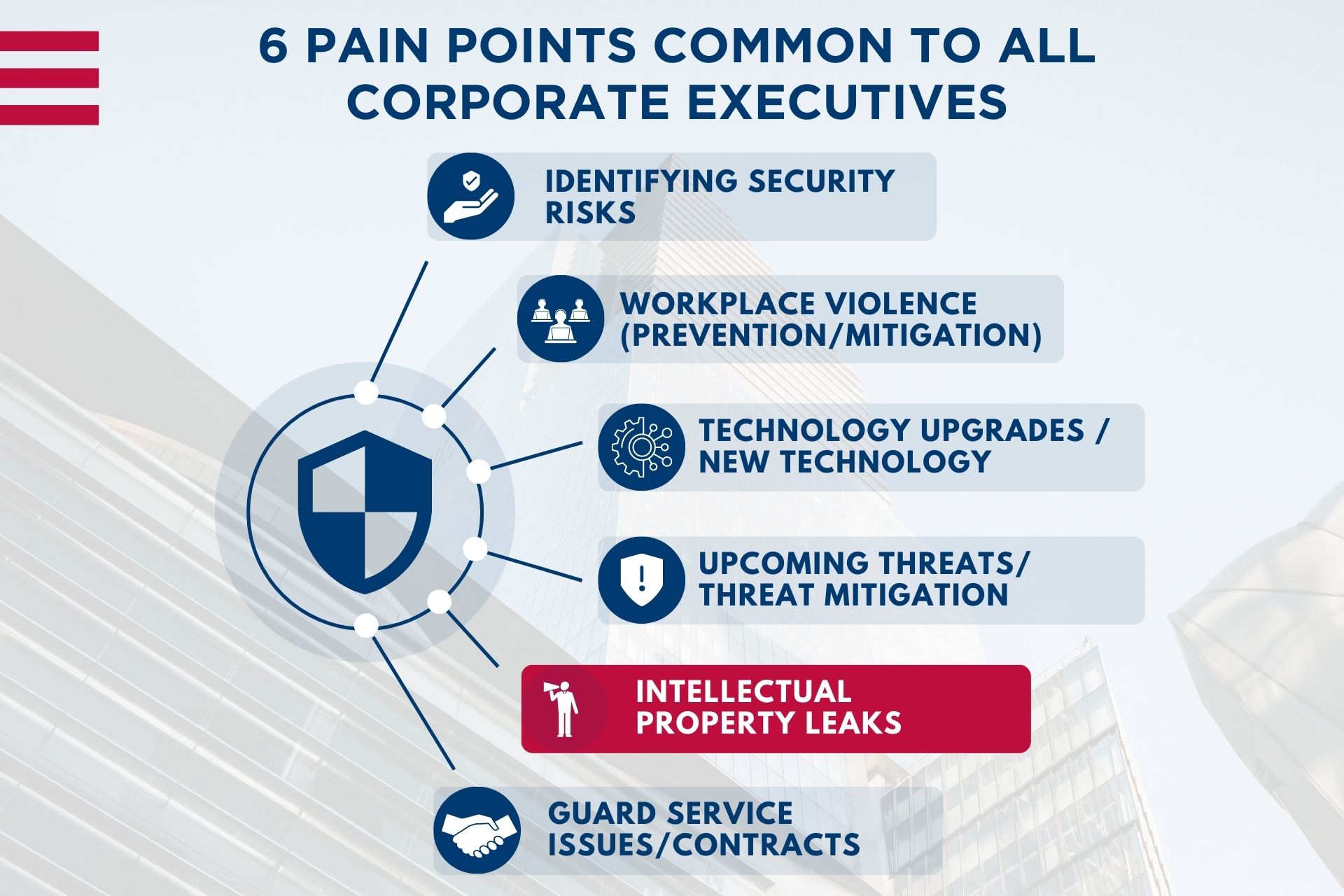
Adversarial government spying. Insider espionage. Corporate Boards authorizing money to be spent on spying programs of rival corporations. If you think no one would spy on you to get your company secrets, then you are in serious trouble. At the small-to-medium size business, the statement we often hear is “I don’t have anything anyone would want. It really doesn’t have any value”. At the Fortune 500 and above levels, it’s “we have policies and protocols in place”. Sometimes, nothing happens. Unfortunately, when it does, it’s already too late; and then we hear about a “problem” which may exist. Corporate reputations are damaged, sometimes beyond repair. How does it get to this state?
While there are many ways intellectual property can be leaked out of a company, I would like to address four simple, yet deadly ways information is surreptitiously obtained.
Our comprehensive training programs empower your employees to recognize and defend against unauthorized access and manipulation, ensuring the confidentiality of your sensitive information. Ask for more information.
By understanding these points, individuals and organizations can take necessary steps to protect their intellectual property and prevent leaks from happening.
Rest assured, PCC Secure is well-versed in navigating such complex challenges. Our seasoned experts will guide you through the implementation of strong policies, protocols, and preventive measures to tackle insider threats effectively. We understand the importance of your peace of mind and are committed to being your trusted advisor in the world of security. Together, we will fortify your corporate defenses, ensuring the confidential nature of your intellectual property remains intact.
If you would like to discuss any of the pain points described above, we encourage you to call our office at 914-576-8706 to set up a free consultation session.
Is your business prepared to face today’s ever-evolving security risks? Learn how to identify and overcome critical threats with our previous blog post: Safeguard Your Business: Identifying & Overcoming Critical Security Risks (Part 1 of 6).
Don’t forget to subscribe to PCC Insights to get email notification when we post our next blog!

Unlock the full potential of your security and risk management with our expert-guided STAR Power Sessions. Get personalized coaching tailored to your organization’s unique needs. Don’t leave your business vulnerable – Book Your STAR Power Session Now!

