The headlines in today’s newspapers read pretty much the same every day. Mass shootings, cyber-
attacks, data breaches, identity theft. Not to mention the weekly mentioning of corruption within our
government. Noise, what I am calling it, is becoming background sounds we don’t pay attention to once we realize it is there. We shake our heads when seeing the headlines in faint disbelief, then discount it quickly. Just like that air conditioner running and humming in the background where you are reading this is ignored, so is the noise of today. Whether it’s the frequency of what we are reading, hearing, or seeing, we are becoming desensitized to it all. It is all becoming white noise.
With today’s economy, corporate executives are forced to face challenges to prioritize their time, money, and limited resources against the pressures of dropping stock prices, Board pressures to increase sales, shrinkage from theft, and a human resource conundrum never seen in the business
world.
There is no time to stop, look, and listen to the noise.
I believe this is the real threat. We are so caught up in our worlds, that we are not seeing the threats we need to recognize, plan for, and react to. As we say in crisis management, the day we meet for the first time should never be at the scene of a crisis. So, what is an example of a threat we may be facing but are not hearing? “Chips”. Electronic chips, necessary in most electronic devices, from critical military defense, to cars, to household appliances, to security devices. Our supplies come from Taiwan. If China, as reports indicate, was to enter Taiwan and take it over, our supply of chips would be virtually stopped. Current intel estimates indicate it would be about a two-year period before supply chains can be fulfilled. In the security world, this can mean two years before parts, such as computer switches, nodes, servers, etc., can be replaced. Today, it takes about 90 – 120 days to get electrical security components. If our supply chain is slowed down or stopped, we can be looking at a two-year wait. Although the Federal government is trying to create chip manufacturing within CONUS, sufficient supply to meet the demand is years away.
How can you mitigate the potential effects of having your access control, video and visitor management systems go down for months? Here are some suggestions:
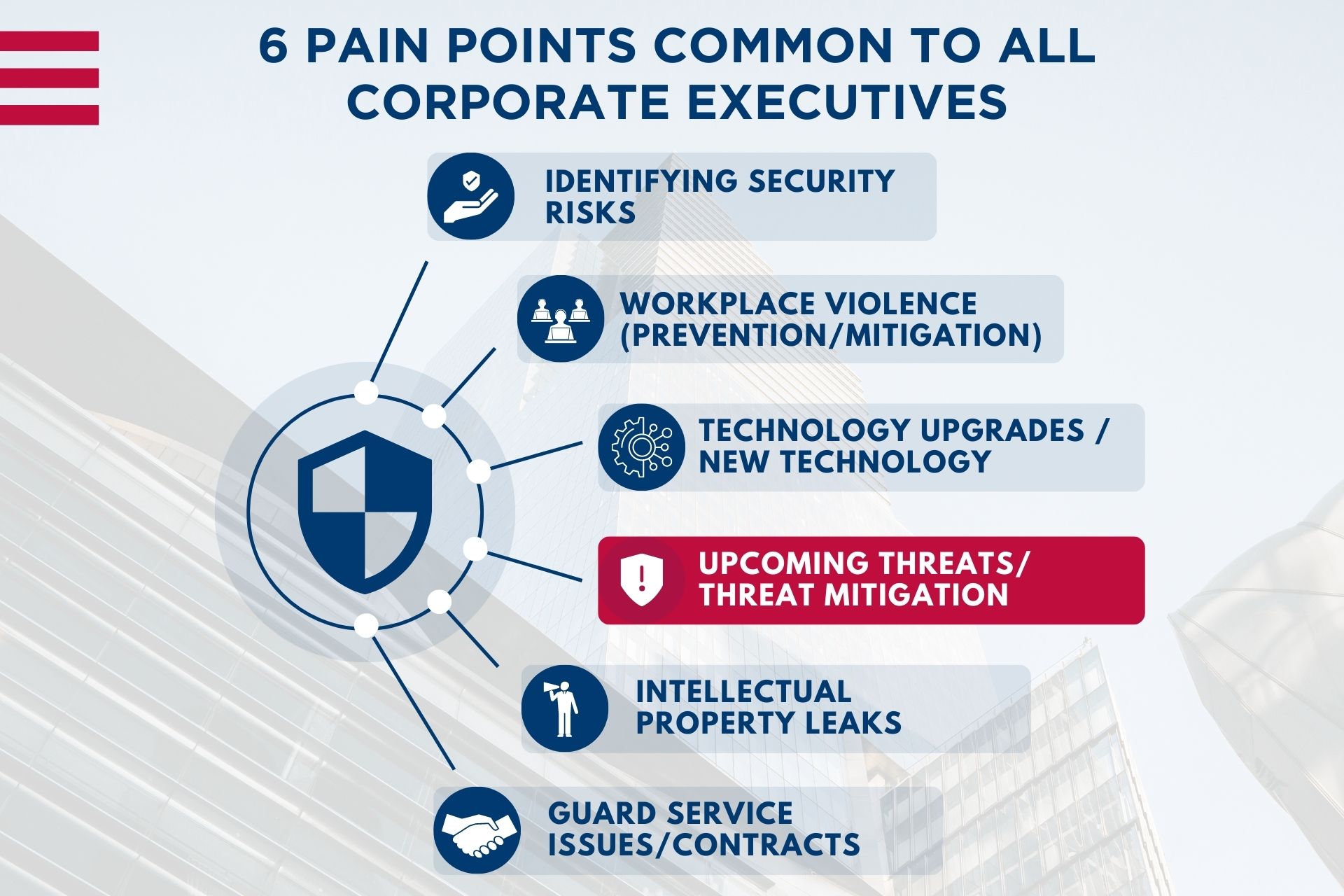
Is your business prepared to face today’s ever-evolving security risks? Learn how to identify and overcome critical threats with our previous blog post: Safeguard Your Business: Identifying & Overcoming Critical Security Risks (Part 1 of 6).
If you would like to discuss any of the pain points described above, we encourage you to call our office at 914-576-8706 to set up a free consultation session.
Don’t forget to subscribe to PCC Insights to get email notification when we post our next blog!

Unlock the full potential of your security and risk management with our expert-guided STAR Power Sessions. Get personalized coaching tailored to your organization’s unique needs. Don’t leave your business vulnerable – Book Your STAR Power Session Now!

